Ransomware is a type of malware that prevents or limits users from accessing their system. This type of malware forces its victims to pay the ransom through certain online payment methods in order to grant access to their systems, or to get their data back. Some ransomware encrypts files (called Cryptolocker). Other ransomware use TOR to hide C&C communications (called CTB Locker).
The ransom prices vary, ranging from $USD 24 to more than $USD 600, or even its bitcoin equivalent. It is important to note, however, that paying for the ransom does not guarantee that users can eventually access the infected system.
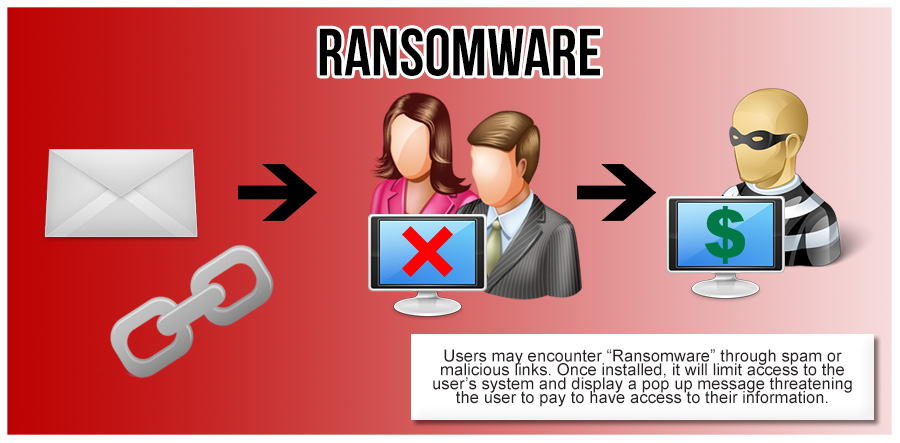
Users may encounter this threat through a variety of means. Ransomware can be downloaded by unwitting users by visiting malicious or compromised websites. It can also arrive as a payload, either dropped or downloaded by other malware. Some ransomware are delivered as attachments to spammed email.
Once executed in the system, a ransomware can either (1) lock the computer screen or (2) encrypt predetermined files with a password. In the first scenario, a ransomware shows a full-screen image or notification, which prevents victims from using their system. This also shows the instructions on how users can pay for the ransom. The second type of ransomware locks files like documents, spreadsheets and other important files.
Ransomware is considered a “scareware” as it forces users to pay a fee (or ransom) by scaring or intimidating them. In this sense, it is similar to the FAKEAV malware, though using a different tactic. Instead of capturing the infected system or encrypting files, FAKEAV coax users into purchasing their bogus anti malware software by showing fake anti malware scanning results.
Known Ransomware Families
Below are known ransomware families:
| Family Name | Aliases | Description |
| ACCDFISA | Anti Cyber Crime Department of Federal Internet Security Agency Ransom | First spotted early 2012; Encrypts files into a password-protected; Cybercriminals behind this ransomware asks payment thru Moneypak, Paysafe, or Ukash to restore the files and unlock the screen; Known as a multi-component malware packaged as a self-extracting (SFX) archive; May come bundled with third party applications such as Sdelete andWinRAR |
| ANDROIDOS_LOCKER | First mobile ransomware spotted; Uses Tor, a legitimate service that allows anonymous server connections; Users with mobile devices affected by this malware may find the files stored in their mobile device rendered useless and held for ransom | |
| CRIBIT | BitCrypt | Similar to CRILOCK with its use of RSA-AES encryption for target files; Version 1 uses RSA-426; Version 2 uses RSA-1024; Appends the string bitcryp1 (for version 1) and bitcrypt2(for version 2) to the extension name of the files it encrypts |
| CRILOCK | CryptoLocker | Employs Domain Generation Algorithm (DGA) for its C&C server connection; October 2013 – UPATRE was found to be the part of the spam mail that downloads ZBOT, which further downloads CRILOCK |
| CRITOLOCK | Cryptographic locker | Uses advanced encryption standard (AES-128) cryptosystem; The word Cryptolocker is written in the wallpaper it uses to change an affected computer’s wallpaper |
| CRYPAURA | PayCrypt | Encrypts files and appends the corresponding email address contact for file decryption; PayCrypt version appends .id-{victim ID}[email protected] to files it encrypts |
| CRYPCTB | Critroni, CTB Locker, Curve-Tor-Bitcoin Locker | Encrypts data files; Ensures there is no recovery of encrypted files by deleting its shadow copies; Arrives via spam mail that contains an attachment, actually a downloader of this ransomware; Uses social engineering to lure users to open the attachment; Uses Tor to mask its C&C communications |
| CRYPDEF | CryptoDefense | To decrypt files, it asks users to pay ransom money in bitcoin currency |
| CRYPTCOIN | CoinVault | Encrypts files and demands users to pay in bitcoin to decrypt files; Offers a one-time free test to decrypt one file |
| CRYPTFILE | Uses unique public key generated RSA-2048 for file encryption and also asks users to pay 1 bitcoin to obtain private key for decrypting the files | |
| CRYPWALL | CryptoWall, CryptWall, CryptoWall 3.0, Cryptowall 4.0 | Reported to be the updated version of CRYPTODEFENSE; Uses bitocin currency as mode of payment; Uses Tor network for anonymity purposes; Arrives via spam mail, following UPATRE-ZBOT-RANSOM infection chain; CryptoWall 3.0 comes bundled with FAREIT spyware; Cryptowall 4.0 encrypts file name of files it encrypts and follows an updated ransom note, it also comes from spam as a JavaScript attachment, and may be downloaded by TROJ_KASIDET variants |
| CRYPTROLF | Shows troll face image after file encryption | |
| CRYPTTOR | Changes the wallpaper to picture of walls and asks users to pay the ransom | |
| CRYPTOR | batch file ransomware | Arrives thru DOWNCRYPT; A batch file ransomware capable of encrypting user files using GNU Privacy Guard application |
| DOWNCRYPT | batch file ransomware | Arrives via spam email; Downloads BAT_CRYPTOR and its components such as a decoy document |
| VIRLOCK | VirLock, VirRansom | Infects document files, archives, and media files such as images |
| PGPCODER | Discovered in 2005; first ransomware seen | |
| KOLLAH | One of the first ransomware that encrypts files using certain extension names; Target files include Microsoft Office documents, PDF files, and other files deemed information-rich and relevant to most users; Adds the string GLAMOUR to files it encrypts | |
| KOVTER | Payload of the attack related to YouTube ads that lead to the Sweet Orange exploit kit | |
| MATSNU | Backdoor that has screen locking capabilities; Asks for ransom | |
| RANSOM | Generic detection for applications that restrict the users from fully accessing the system or encrypts some files and demands a ransom in order to decrypt or unlock the infected machine | |
| REVETON | Police Ransom | Locks screen using a bogus display that warns the user that they have violated federal law; Message further declares the user’s IP address has been identified by the Federal Bureau of Investigation (FBI) as visiting websites that feature illegal content |
| VBUZKY | 64-bit ransomware; Attempts to use Shell_TrayWnd injection; Enables TESTSIGNING option of Windows 7 | |
| CRYPTOP | Ransomware archiver | Downloads GULCRYPT and its components |
| GULCRYPT | Ransomware archiver | Archives files with specific extensions; Leaves a ransom text file containing the instructions on who to contact and how to unpack the archives containing user’s files |
| CRYPWEB | PHP ransomware | Encrypts the databases in the web server making the website unavailable; Uses HTTPS to communicate with the C&C server; Decrypt key is only available in the C&C server |
| CRYPDIRT | Dirty Decrypt | First seen in 2013 before the emergence of Cryptolocker |
| CRYPTORBIT | Detection for images, text, and HTML files which contain ransom notes that are indicators of compromised (IOC) | |
| CRYPTLOCK | TorrentLocker | Poses as CryptoLocker; newer variants display crypt0l0cker on the affected computer; uses a list of file extensions that it avoids encrypting, compared to usual ransomware that uses a list of file extensions to encrypt – this allows CRYPTLOCK to encrypt more files while making sure the affected computer still runs, ensuring users know that their files are encrypted and access to the Internet to pay the ransom is still present |
| CRYPFORT | CryptoFortress | Mimics TorrentLocker/CRYPTLOCK user interface; Uses wildcards to search for file extensions; encrypts files in shared folders |
| CRYPTESLA | TeslaCrypt | User interface is similar to CryptoLocker; encrypts game-related files; Versions 2.1 and 2.2 appends encrypted files with .vvv and .ccc; Version 3.0 has an improved encryption algorithm and appends .xxx, .ttt, and .mp3 to files it encrypts |
| CRYPVAULT | VaultCrypt | Uses GnuPG encryption tool; downloads hacking tool to steal credentials stored in web browsers; uses sDelete 16 times to prevent/hinder recovery of files; has a customer support portal; is a batch script crypto-ransomware |
| CRYPSHED | Troldesh | First seen in Russia; added English translation to its ransom note to target other countries; aside from appending .xtbl to the file name of the encrypted files, it also encodes the file name, causing affected users to lose track of what files are lost |
| SYNOLOCK | SynoLocker | Exploits Synology NAS devices’ operating system (DSM 4.3-3810 or earlier) to encrypt files stored in that device; has a customer support portal |
| KRYPTOVOR | Kriptovor | Part of a multi-component infection; aside from its crypto-ransomware component, it has an information stealing component that steals certain files, processes list, and captures desktop screenshot; uses an open source Delphi library calledLockBox 3 to encrypt files |
| CRYPFINI | CryptInfinite, DecryptorMax | Arrives via spam with macro attachment, the spam mail usually pretends to be a job application linked to a Craigslist post; Appends .crinf files |
| CRYPFIRAGO | Uses Bitmessage for communication with its creators; Appends .1999 or .bleep to files it encrypts | |
| CRYPRADAM | Radamant | May arrive via exploit kits; Appends .rdm to files it encrypts |
| CRYPTRITU | Ransom32 | Known as the JavaScript ransomware |
| CRYPBOSS | CrypBoss | Appends .crypt to files it encrypts |
| CRYPZUQUIT | Zuquitache, Fakben | Known as the ransomware-as-a-service (RaaS) malware |
| CRYPDAP | PadCrypt | Has live chat support for affected users; Arrives via spam |
| CRYPHYDRA | HydraCrypt | Based on leaked source code of CrypBoss; Arrives via spam |
| LOCKY | Locky | Renames encrypted files to hex values; Appends .locky to files it encrypts; Arrives via spam with macro-embedded .DOC attachment, similar to the arrival of DRIDEX malware |
| CERBER | Cerber | Encrypts the file name and appends it with .cerber; Drops a .VBS file that makes the computer speak to the victim |
| CRYPSAM | SAMSAM | Uses exploits on JexBoss open source server application and other Java-based application platforms to install itself in targeted Web application servers |
| PETYA | Petya | Causes blue screen and displays its ransom note at system startup |
What Can Users Do?
Prevention
Users infected by ransomware should do the following:
- Disable System Restore. The main purpose of disabling system restore is to be able to scan system volume information folder.
- Run your anti-malware to scan and remove ransomware-related files.
Note that some ransomware requires extra removal steps such as deleting ransomware files in Windows Recovery Console. Be sure to follow all required steps to completely remove the specific ransomware your computer has.
To prevent ransomware infections, keep these things in mind:
- Backup your files regularly.
- Apply software patches as soon as they become available. Some ransomware arrive via vulnerability exploits.
- Bookmark trusted websites and access these websites via bookmarks.
- Download email attachments only from trusted sources.
- Scan your system regularly with anti-malware.


Follow Us