Network / PCI ASV Vulnerability Scanning
Cloud based PCI DSS approved network vulnerability scanning solutions to identify vulnerabilities in systems, network devices, applications and databases.
- PCI ASV accredited for accurate internal and external vulnerability scanning
- Demonstrate compliance with PCI DSS, FISMA, HIPAA and GLBA
- Easy to manage: no hardware, no software, and no maintenance
- Non-intrusive scanning of physical and cloud infrastructure
- Prioritized remediation plan with dedicated support
Ready to Get Started?
Get in touch with our expert team to discuss your business needs or to evaluate the services for free.
Address security concerns with on demand network vulnerability scanning
Advanced Network Vulnerability Scanning, with multi platform support
Highly scalable, Internal and External vulnerability scanning over the internet anytime from anywhere that identify over 60,000+ vulnerabilities across your entire network and supported cloud environments with constantly updated vulnerability database
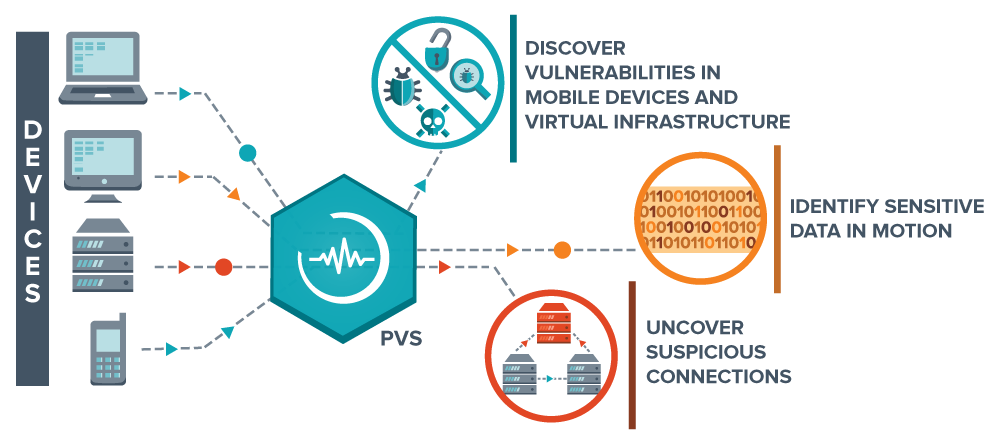
- Operating systems: Windows, OS X, Linux, Solaris, FreeBSD, Cisco iOS, IBM iSeries
- Databases: Oracle, SQL Server, MySQL, DB2, PostgreSQL, MongoDB
- Virtualization: VMware ESX, ESXi, vSphere, vCenter, Microsoft, Hyper-V, Citrix Xen
- Cloud: Scans the configuration of cloud apps like Salesforce and instances like AWS and Rackspace
- Configuration auditing: CERT, CIS, COBIT/ITIL, DISA, STIGs, FDCC, ISO, NIST, NSA
- Web applications: Web servers, web services, OWASP vulnerabilities
- Malware detection:Discover potentially unwanted and unmanaged software
- Compliance auditing: FFIEC, FISMA, CyberScope, GLBA, HIPAA/ HITECH, NERC, PCI, SCAP, SOX

Quarterly Network vulnerability scanning for PCI DSS and other regulatory compliance
If you handle credit card data, you must be PCI compliant. To achieve and maintain PCI compliance, you must perform quarterly network vulnerability scanning. This is true for small and large companies alike. Failure to comply can result in large fines and losing the ability to process credit and debit card payments. Our security team specializes in helping SMBs and Mid-Markets understand and comply with the PCI Data Security Standard (DSS) regulations. We can help your organization reduce the risk of a security breach.
Many regulations, including PCI DSS, SOX, GLBA, HIPAAFFIEC, NERC CIP and FISMA, require organizations to test regularly for network security vulnerabilities. Our vulnerability scanning solution helps identifying and mitigating information security risk.
Research-driven Network Vulnerability Management
Easy ownership with dedicated security expert team
The fully managed network vulnerability scanning service eliminates administrative overhead by providing complete operational support, from configuring the technology and scheduling scans to expert review of results, virtually eliminating false positives.
By identifying the vulnerabilities in your environment and providing detailed analysis and remediation guidance, our network vulnerability scanning service helps you reduce your exposure, comply with regulations and safeguard your business.
Our experts apply their extensive knowledge and experience to verify and supplement the automated results with a manual review to eliminate false positives to ensure the results are of the highest fidelity to ensure reports produced contain rich, actionable intelligence including detailed descriptions of network vulnerability, insight into root cause, and available workarounds.
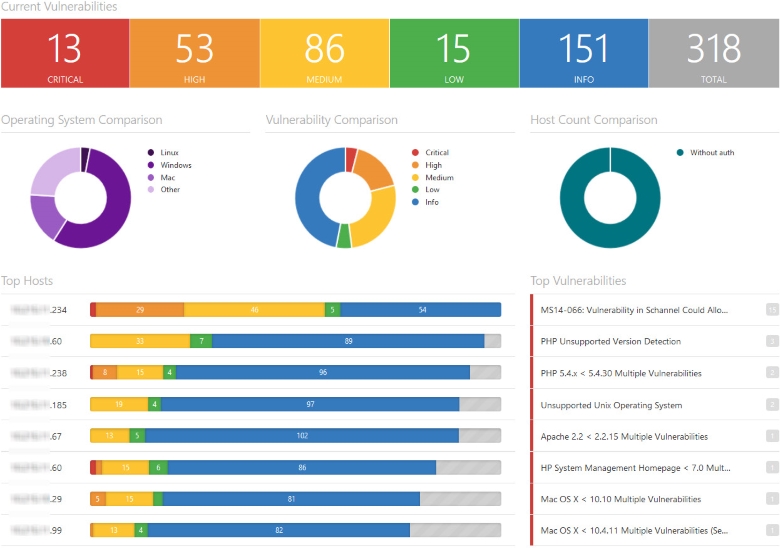
Comprehensive Reporting with remediation tracker support
Once you’ve performed vulnerability scanning of your assets for vulnerabilities, you need to develop a response plan that describes the vulnerabilities and their potential impact to your environment, and then decide which issues to remediate first. Doing this efficiently requires expert knowledge of not only the exploit methods but the affected systems as well.
Along with an array of remediation reports that provide security managers with a current snapshot of remediation status and progress, also Includes a highly automated, integrated remediation and trouble-ticketing workflow system.
Resources

We’re here to help 24x7x365.
Get in touch with our expert team to discuss your business needs.










