Firewall Security Assessment
Firewall Security Assessment helps you gain visibility on firewall configuration and access lists to secure, optimize, comply with regulations and manage to keep them secure from external threats.
- Support wide range of firewall’s and network devices
- Secure upload and confidential handling of your exported configuration file
- Demonstrate PCI DSS, SOX, ISO, NSA, NERC and FISMA compliance
- Prioritized remediation plan with dedicated expert guidance
- No remote access or credentials required
Ready to Get Started?
Get in touch with our expert team to discuss your business needs or to evaluate the services for free.
Firewall Security Assessment: Key Features
Comprehensive, Multi-Vendor Firewall Support
Firewall and Network device configuration assessment that supports the most comprehensive list of firewall vendors and enterprise workflow solutions
- Cisco® Security Appliances: PIX, ASA, FWSM, ASA 8.4
- Cisco IOS routers: Version 12.0 to 12.4, excluding IOS XE
- Juniper® firewalls: Netscreen, SSG, ISG, SRX
- Check PointTM products: SmartCenter NG/NGX, Security Management R70
- Check PointTM platforms: SecurePlatform, Check Point IPSO (formerly Nokia), Crossbeam, Linux, Solaris


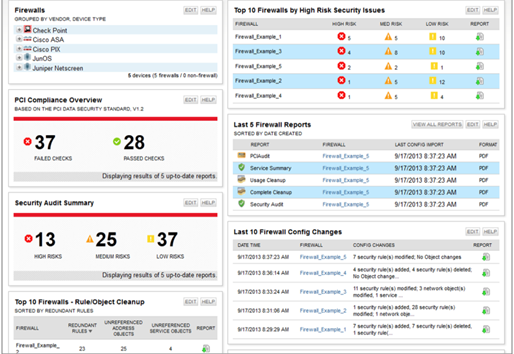
Firewall Policy Compliance
Firewall Security Assessment, ensures compliance with industry best practices, regulations and custom policies, including PCI DSS, SOX, ISO, NSA, NERC and FISMA with audit reports and compliance scorecards.
Scalable solution that lets you maintain continuous firewall compliance with automated, daily compliance checks for your entire enterprise.
Firewall Security Assessment with Well-defined, repeatable, and consistent methodology
Review the firewall device configuration, looking at industry best practices and hardening techniques, and interprets the rulesets by understanding the overall company architecture and will:
– Review the firewall configuration file for the identification and protection of all network segments.
– Review the processes and mechanisms for a security model that denies access by default.
– Review the implementation of open ports and services for all access points to the external presence.
– Review the documentation of those entries and the configuration of those ports and services.
– Identify the implementations of banners, access controls, and appropriate use policies.
– Review the implementation of processes for monitoring and logging access at access points to the network.
– Review controls for default accounts, passwords, and network management community strings.
– Review all ingress/egress points within the network.
– Identify best practices implementation and lack of hardening techniques.

Support a broad range of industry leading security solutions platforms, including:
Comprehensive Reporting with remediation tracker support
Firewall and Network device configuration assessment comprehensive reporting is with Executive Summary and detailed vulnerability analysis, recommendations with prioritized action plan. The Reporting address the Regulatory requirements including PCI DSS, SOX, ISO, NSA, NERC and FISMA Compliance.
Resources

We’re here to help 24x7x365.
Get in touch with our expert team to discuss your business needs.