Mobile App Security Assessment
Mobile Application Security Assessment Service Identify vulnerabilities, malicious or potentially risky actions in mobile applications and help you to prioritize, re mediate and secure your mobile apps before deployment.
- Include both static and dynamic mobile security testing techniques
- Easy to manage: no hardware, no software, and no maintenance
- OWASP Top 10 Mobile framework to comply PCI and HIPPA
- Support for iOS, Android, Blackberry,and Windows
- Unique Behavioral analysis and privacy checks
Ready to Get Started?
Get in touch with our expert team to discuss your business needs or to evaluate the services for free.
Featured customers securing their Mobile Apps
Identify and fix mobile app security vulnerabilities as they are created
E Com Security Solutions mobile app security assessment delivers coverage across the complete mobile app environment, from the local app running on-device to the back-end web services and RESTful APIs that power mobile apps off-device. The Security Assessment ruleset includes standards such as OWASP Top 10 for Mobile, PCI DSS, HIPPA and others. Using a combination of manual and dynamic analyses along with custom harnesses for automated fuzzing, the mobile app security assessment provides verification and validation across all major control categories, including authentication, session management, access control, malicious input handling, cryptography at rest, and much more.
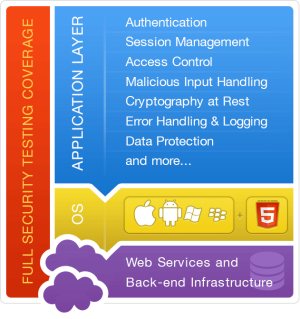

Reputation testing and Unique behavioral analysis in Mobile App Security Assessment
Mobile Reputation Management service provides privacy checks for iOS and Android applications, either company owned or those applications deployed from the App Store. If an app isn’t in our database, the request process is easy – just provide the app information or upload a binary.
Behavioral Analysis looks for malicious behaviors and privacy leaks with over 18 check categories including: use of insecure libraries, accessing or writing private data to insecure logs and directories, and reputation analysis on all traffic endpoints.
Three-tier Mobile App Security Approach
Mobile client assessment areas include: File system, Memory, Run-time tampering, Input validation, Source code analysis, Binary analysis and Inter-application communication.
Mobile network traffic assessment areas include: Transport layer security, Data stream analysis, Malware analysis and Host communication enumeration
The web server side is examined after, and leverages everything learned from, evaluation of the client and network portions of the application. Testing steps include: Mobile Web application vulnerability assessment, Mobile SOAP1 or REST2-based Web service testing and Static analysis of any back-end code

Comprehensive Reporting to Meet Compliance Requirements
Centralized reporting system provides real-time visibility into overall security status and processes. Reports include links to documentation to help development teams understand programming best practices. With references to standards, such as Common Weakness Enumeration (CWE), reports outline and document improvements–helping you determine what additional actions are needed to safeguard security.
Generate compliance mobile app security assessment reports, including PCI Data Security Standard (PCI DSS), Payment Application Data Security Standard (PA-DSS), ISO 27001 and ISO 27002, HIPAA, Gramm–Leach–Bliley Act (GLBA) and Basel II.
Resources

We’re here to help 24x7x365.
Get in touch with our expert team to discuss your business needs.











