Infrastructure Security Solutions
E Com Infrastructure Security solutions include network security and cloud security services to provides a comprehensive evaluation of your existing network and cloud infrastructure security landscape in relation to industry best practices and regulatory requirements.
Assess your Infrastructure Security and create a road map to reduced risk
Understanding the state of your current Infrastructure Security capabilities and identifying vulnerabilities are the first steps toward protecting the con-confidentiality, integrity and availability of critical data. These steps are also integral to regulatory compliance efforts.
Remaining unaware of Infrastructure Security risks can leave your organization vulnerable to attacks targeting the network, or a breach resulting in the loss, misuse or exposure of sensitive data. You may experience significant costs to address the attack or breach and in a loss of customer trust and damaged reputation. To establish an effective security strategy, you must start with an accurate evaluation of your current Infrastructure Security posture.
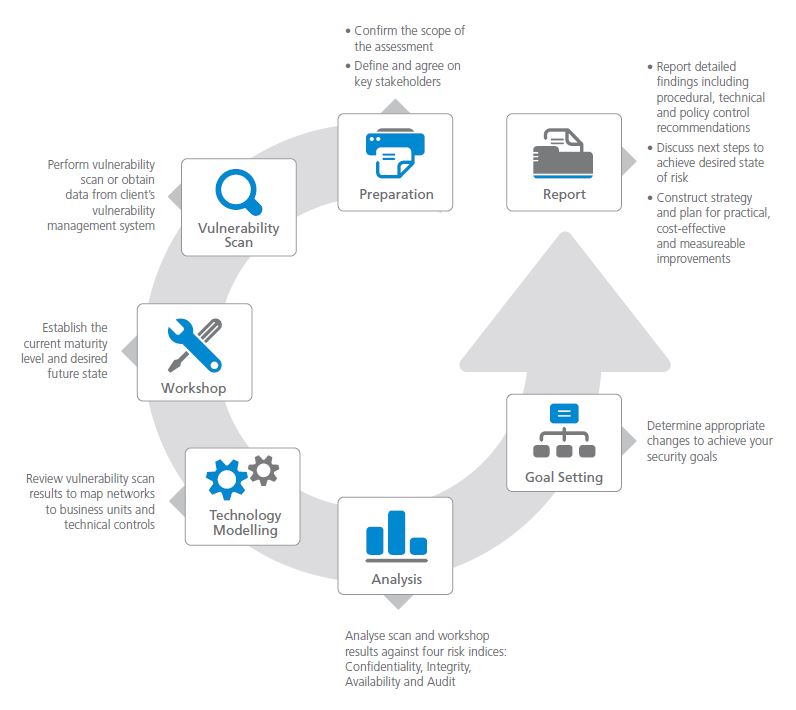
Network / PCI ASV Vulnerability Scanning
E Com Security Solutions vulnerability scanning and management services help you to understand your organization’s exposure to attack and compromise from network borne malware attacks and protect organizations by identifying and reporting network security vulnerabilities that can be exploited by cyber criminals.
PCI ASV Scanning technology and industry leading forensics and security research team, provides current and up-to-date intelligence for optimal and effective scanning support.


Network Penetration Testing
Evaluate Your Security Stance, Think Like an Attacker
The most accurate method to evaluate your organization’s information security stance is to observe how it stands up against an attack. Our experts perform a simulated attack on your network to identify faults in your system, but with care to help ensure that your network stays online. We follow a structured methodology to ensure a thorough test of your entire environment and meet regulatory requirements as PCI DSS, GLBA, HIPAA, SOX, FISMA/NIST.
Firewall / VPN Security Review
Gain visibility on firewall configuration and access lists to secure, optimize, comply with regulations and manage to keep them secure from external threats.
During firewall review, we will examine vendor specific vulnerabilities, ingress and egress access controls, logging and auditing, and system management. This review also helps avoid malicious infiltration and ensures true end-to-end security with the Virtual Private Network (VPN) Security Assessment.


Cloud Security Assessment
Cloud computing offers several key advantages to organizations. These include reduced costs, automation, hardware independence, high availability and increased flexibility. Use of cloud technology also alters the risk landscape in areas such as confidentiality, privacy, integrity, regulatory compliance, availability and e-discovery. Therefore, it is important to ensure that proper security assurances are in place.
Depending on where you are in your cloud journey, we have security services to help protect your data and applications. Highly trained consultants can provide guidance ensuring the integrity and compliance of your cloud deployments with mandates and best practices.
Have you already been compromised?
In 93% of cases, it took attackers minutes or less to compromise systems. Organizations, meanwhile, took weeks or more to discover that a breach had even occurred—and it was typically customers or law enforcement that sounded the alarm, not their own security measures.
100,000+ incidents. Analysis of 2,260 breaches. 82 countries. 67 contributing organizations.
Confirmed data breaches involved leveraging weak, default or stolen passwords.
Caused by a shortage of server capacity, where non-malicious spikes in web traffic overwhelm systems and cause key applications to crash.
Misuse by insiders, outsiders (due to collusion) and partners granted privileged access to systems.
Ransomware incidents which involves attackers encrypting the contents of a device, rendering it useless demanding ransom to unlock the data.
Attacks motivated by espionage carried out by state-affiliated actors, often looking for intellectual property.
Point-of-sale (POS) intrusions compromising the computers and servers that run POS applications, with the aim of capturing payment data.
Extend your team with experts
E Com Security Solutions specializes in creating pragmatic, cost-effective and strategic security assessment engagements to help our clients achieve sound governance, risk management and compliance. We help you determine your priorities, and tailor our approach to deliver on both immediate and longer-term goals.