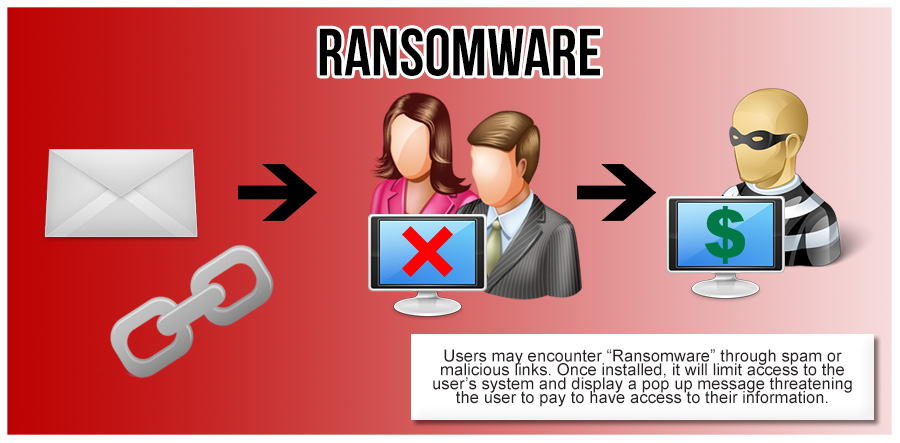
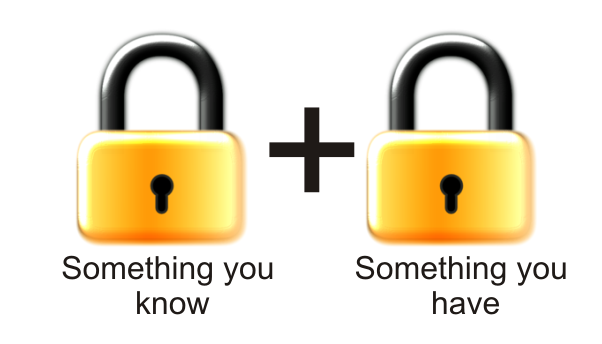
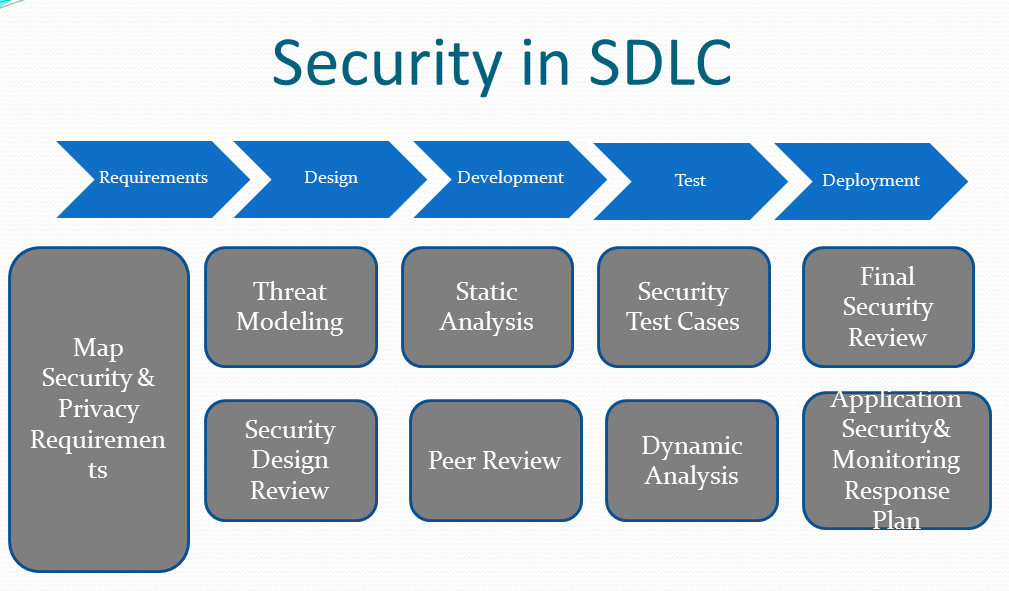
How to achieve HIPAA Compliance for Medical Software applications?
In relation to medical software applications, the term HIPAA compliant means that the application meets the technical and physical safeguards of the HIPAA Security Rule. If you are hosting an application in a HIPAA-compliant environment then it does not make the application HIPAA-compliant. If you build an eHealth or mHealth app that collects personal data [...]