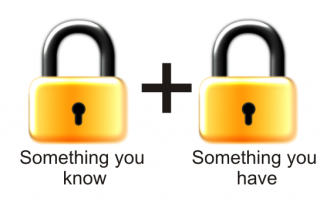
FBI Cyber Warning: Ignore Your CEO’s E-Mail And Phone Her Back — Or Your Company May Pay For It
The FBI is warning people about a business email scheme which has resulted in huge losses to companies in Phoenix and other U.S. cities. Here’s how the scam works: A CEO seemingly emails an employee — typically in a finance or administrative role — instructing them to perform a wire transfer. The employee follows directions [...]